Modern Wi-Fi access points have an array of features available to you for securing your wireless network. Unfortunately, only a few of these are effective at actually stopping sophisticated network intruders with any level of success.
Why worry about Wi-Fi security?
If an unauthorised person gains access to your network, they can cause a lot of trouble. This includes:
- Using your network connection for egress to other networks, such as the internet. If they were to conduct nefarious actions such as copyright infringement, it would be traced back to you, and in many juristictions you would end up responsible for their unlawful activities.
- Spoofing your wireless access point (e.g. your broadband router) in order to watch, block, or alter network traffic being broadcast to and from all devices on your network, including redirecting users to phishing websites or attempting to infect devices with malware.
- Gaining access to all unprotected network resources; this includes your physically-local network resources such as network drives and printers, but also virtual network resources to which your own network has access, such as those on your corporate intranet or cloud VPC.
Thankfully, there are a few options available to us to protect ourselves. Some are more effective than others.
Hiding the network by not broadcasting the SSID
Summary: not effective, but feel free to use in addition to other techniques if desired
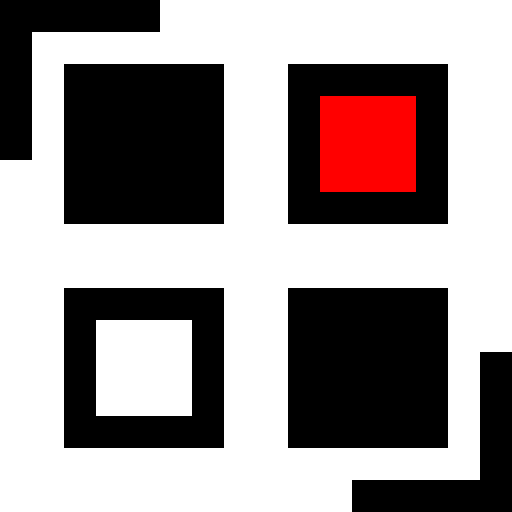
Each Wi-Fi network has an associated SSID (service set identifier), usually displayed as the network name, which is a user-friendly way of differentiating one Wi-Fi network from another. The SSID is the name you see when picking which network to connect to from a list on your device.

By not broadcasting the SSID from the access point, you’re removing the network from this publicly-displayed list. The theory is that if an attacker doesn’t know the network’s SSID, or even the presence of the network in the first place, they won’t know how to connect to the network.
This is a barrier to only the most naïve of attackers. It relies on security through obscurity, and unfortunately the obscurity is effectively absent. The SSID is still included in plaintext in network packets being transmitted between wireless clients and the access point; so, even though the broadcast packets themselves are no longer being sent, an an attacker can easily fire up a packet sniffing tool and grab the SSID.
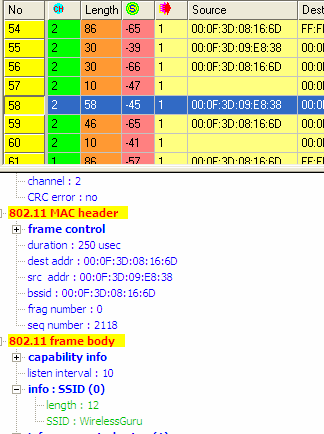
Filtering permitted clients by MAC address
Summary: not effective, but feel free to use in addition to other techniques if desired
Each network device has a hard-coded 48-bit MAC (Media Access Control) address, which is used as a unique identifier to enable devices to be individually addressed on a network. Permitting only certain MAC addresses to communicate with the access point means that only specific devices can connect to the network.
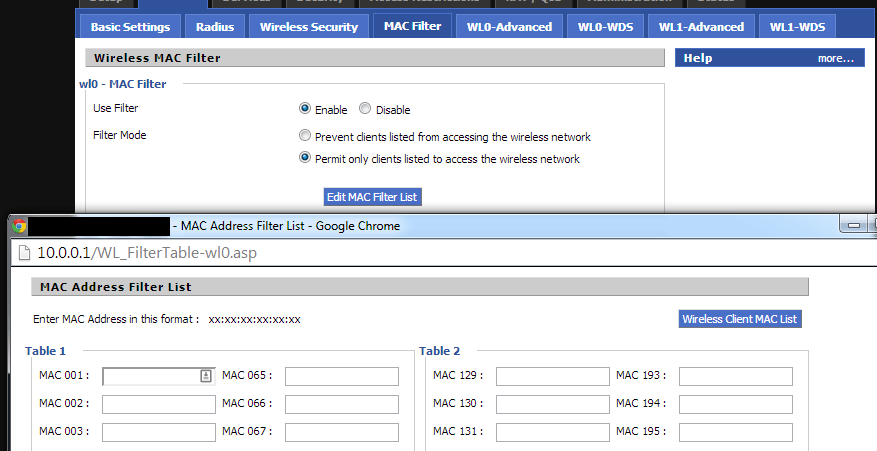
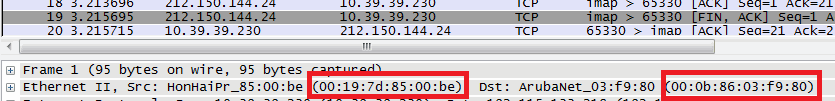
…at least, that’s the theory. It relies on the assumption that a MAC address is unspoofable. Network sniffing tools allow attackers to easily change their MAC address to something other than the default “hard-coded” address. And, since an existing client’s MAC address is already broadcast in the clear (just like the network SSID), it is trivial for an attacker to copy an already-allowlisted MAC address and access the network.
Securing the network with encryption
There are a few different encryption algorithms that are generally available to consumers and businesses.
WEP encryption
Summary: not effective, do not use
WEP (Wired Equivalent Privacy) is an encryption algorithm that was introduced along with the original 802.11 standard.
WEP uses the concept of a pre-shared key, usually in the form of a passphrase that is known to both endpoints. In the consumer market this key is usually printed onto a router’s case, but you are also able to manually set the key to something else of your choosing.
There have been many security issues with WEP over the years, which means that it has now been deprecated in favour of other, more secure encryption algorithms. With modern hardware, it is possible to obtain the encryption key to any WEP-protected network in under 60 seconds.
WPA encryption
Summary: effective, can be used as a fallback, but prefer WPA2 if possible
WPA (Wi-Fi Protected Access) was developed in response to the weaknesses found in WEP. It also implemented a new protocol, TKIP (Temporal Key Integrity Protocol), as part of the 802.11i standard. Although WPA also makes use of a pre-shared key, and still uses the RC4 cipher, it does not suffer from the same cipher flaw as implemented by WEP.
As of 2013, aside from some minor vulnerabilities that have been discovered over the years, the WPA protocol has for the most part remained robust since its introduction in 1999.
WPA2 Personal encryption
Summary: effective, use this in a consumer setting
WPA2 is the technological evolution of WPA. The main difference between WPA and WPA2 is the implementation of the AES cipher for wireless encryption rather than RC4. In the same way that WEP and WPA use a key, the “Personal” variant of WPA2 utilises a pre-shared key to perform authentication. WPA2 is currently considered the gold standard in consumer Wi-Fi technology.
WPA2 Enterprise encryption
Summary: effective, use this in a corporate setting
WPA2 Enterprise is identical to WPA2 Personal in almost every way, the only differences being the use of CCMP and the method of authentication. Instead of utilising a single pre-shared key, the access point can make use of an enterprise service such as a RADIUS server to perform client authentication. The client is then sent a unique encryption key that they can use to connect to the network as normal. This has the added advantage that a user’s use of the network can be controlled with greater fidelity (e.g. remotely revoking access after a given amount of time) by the network administrator.
WPS vulnerabilities
Summary: avoid, it can compromise an otherwise-secure setup
While there have not yet been any serious vulnerabilities found in WPA’s/WPA2’s implementation, their security may nevertheless be compromised by a major security flaw found in WPS (Wi-Fi Protected Setup) in 2011, where access points implementing WPS can have their WPS PIN cracked in under 4 hours using a tool called Reaver, allowing an attacker full access to the encrypted network. (To make things worse, the “Disable WPS” option many manufacturers made available in their configuration screens didn’t actually disable WPS!)
Summary
- Secure your wireless network using techniques that provide real security, rather than the illusion of security.
- WPA2 encryption (Personal or Enterprise) is the best way to protect a wireless network from intruders. WPA encryption can also be used as a reliable fallback if not all devices on the network support WPA2.
- Avoid making use of WPS, as it can compromise an otherwise-secure setup.